OUR SERVICES
Elevate your business
iOne Resources, Inc. specializes in various technological solutions and services. Our offerings include cybersecurity, satellite solutions, infrastructure management, and maritime-related services. Our focus on aspects like security audits, vulnerability prevention, and security analysis, emphasizing cloud security and automation. Our approach encompasses sourcing technology, providing professional services for technology deployment, and offering managed services to maintain and manage IT infrastructure.
The company aims to assist our customers in enhancing digital technology across different domains,
Systems Integration
We provide end-to-end system integration services to design, implement and manage complex IT infrastructure environments no matter the technology or vendor. Our experts seamlessly integrate hardware, software, networks and systems.
Network Solutions
We design, implement and manage high-performance network solutions tailored to your unique business needs. This includes LAN/WAN architecture, traffic optimization, and ensuring robust connectivity.
Cloud Management
Our cloud management services help you migrate and optimize your workloads in the cloud. We ensure your cloud environment is secure, compliant, and provides maximum performance and cost-efficiency.
Cybersecurity
Our cybersecurity services protect your business against evolving cyber threats. We combine cutting-edge technology with expert human intelligence to provide comprehensive security solutions.
Maritime Services
We also offers specialized services in the maritime sector, focusing on navigation, communication, and other technological aspects crucial for maritime operations.
Approach
Our Approach to Security & Prevention
At iOne, we take a proactive and multilayered approach to security and prevention of cyber threats. Our cybersecurity solution is designed to protect against a wide range of attacks, detect anomalies in real-time, and enable rapid response.
We focus on core areas like network security, endpoint protection, access controls, data encryption, vulnerability management, and threat intelligence. Advanced techniques like AI-driven behavioral analysis and deception technology allow us to identify and stop even unknown threats. Strict access controls and data privacy protections prevent unauthorized access. We complement these technical measures with cybersecurity awareness training, disaster recovery planning, and close partnerships with our clients’ IT teams. With constant vigilance and a focus on prevention, we can stay steps ahead of cybercriminals and create robust defense for organizations. Our combination of human expertise and AI-powered detection works 24/7 to provide comprehensive cybersecurity protection.
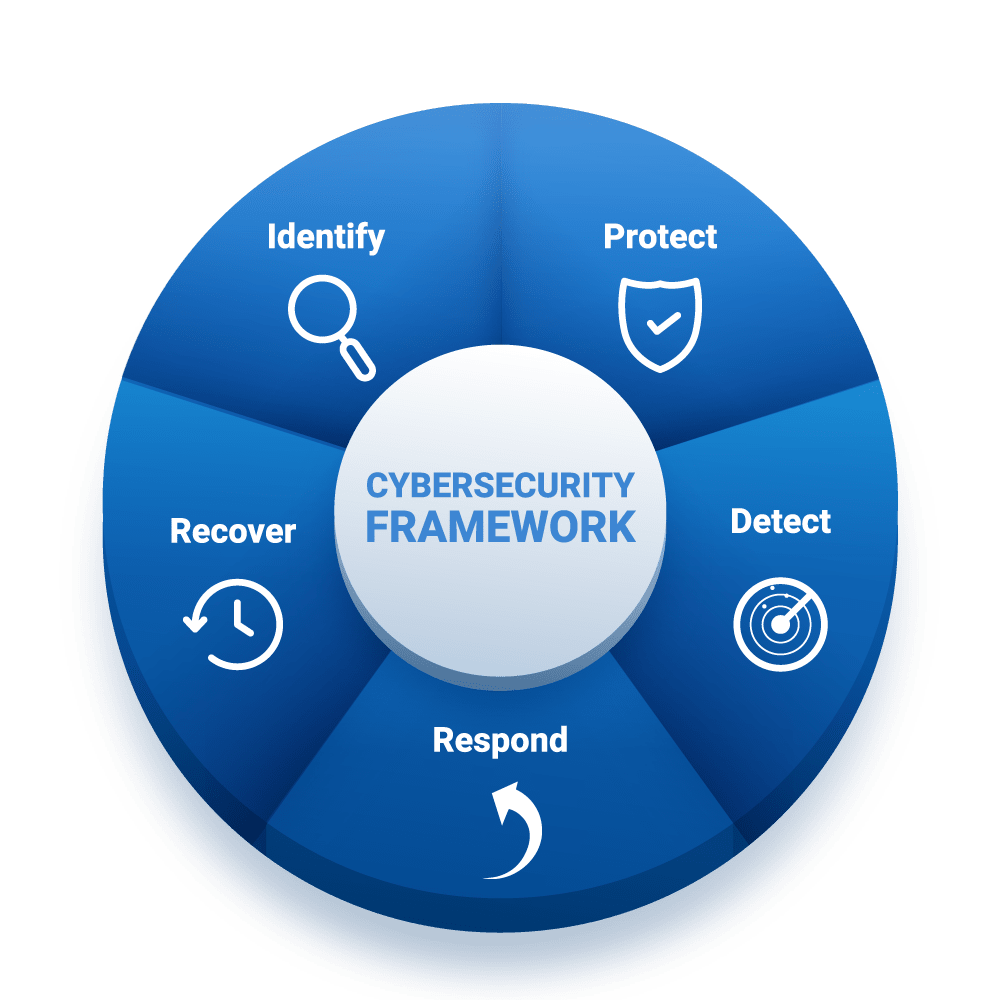
OUR CYBERSEC FRAMEWORK
- Identify: This involves creating an inventory of critical assets and defining the business context, along with identifying potential risk scenarios. It’s about understanding where the organization is most vulnerable.
- Protect: Involves implementing measures like access control, data encryption, and employee training. This step is about establishing defenses against potential threats.
- Detect: Utilizes advanced monitoring tools to quickly identify breaches or suspicious activities, ensuring anomalies are caught early.
- Respond: Establishes a response plan, which might include incident response teams and communication strategies, ensuring swift action in the event of a breach.
- Recover: Focuses on restoring normal operations after an incident, including data recovery and system repairs, and also involves learning from incidents to improve future resilience.
Contact Us
(632) 79105018
1006 The Ceterpoint Bldg, Garnet Road cor J, Vargas Avenue, Pasig City, Philippines
Monday-Friday: 9am – 6pm
Get Started
We are thrilled to hear from you